Article: X-Ray Fault Injection in non-volatile memories on Power OFF devices
Since 2018, the International Conferences on Physical Assurance and Inspection of Electronics (PAINE) gather researchers and practitioners in the field of Hardware Security and Trust to share ideas and solutions to make electronics devices and systems safe and secure. An article by members of our SESAM team was presented by doctoral student Paul Grandamme during the latest edition of the conference that took place last October in Huntsville, Alabama, USA.
In embedded electronic circuits, all permanent data are stored in non-volatile memories such as Flash or EEPROM. Data can be firmware, cryptographic algorithms or keys, access rights and so on. Their security is therefore very important. Such memories are known to be sensitive to fault injection attacks. For many years now, new means of fault injections have been developed (laser or electromagnetic injections, clock or voltage glitches, etc.). The aim of these attacks is to obtain sensitive information or to twist the component from its nominal operation. Almost all of the attacks in the state of the art were carried out on power on devices.
In this paper, we flip bits stored in non-volatile memories of power off devices by X-Ray exposure. We enhance an exponential dependency between the Total Ionizing Dose and the number of errors injected in the memories. An explanation of the physical phenomenon according to the fault model is also proposed. This attack could be an original attack vector in hardware security.
The experiments were carried out with the kind collaboration of Sylvain Girard and Adriana Morana of our MOPERE team.
The work is funded by the Agence Nationale de la Recherche within the framework of the ANR POP project (ANR-21-CE39-0004).
Figure 1 below:
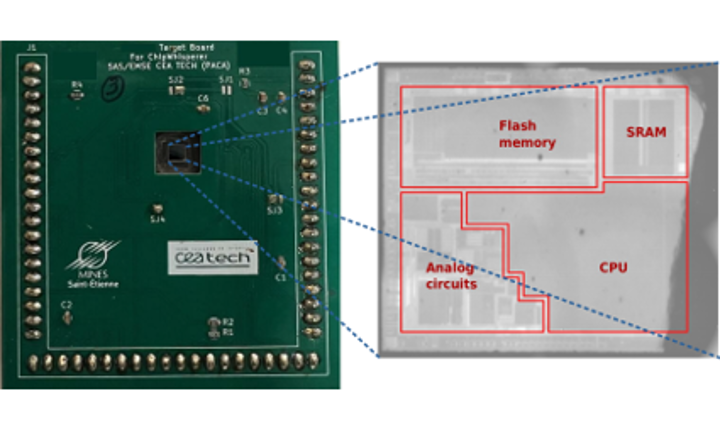
32-bit microcontroller target mount on a custom board and prepare for backside access (left). Infrared image of the DUT (right).
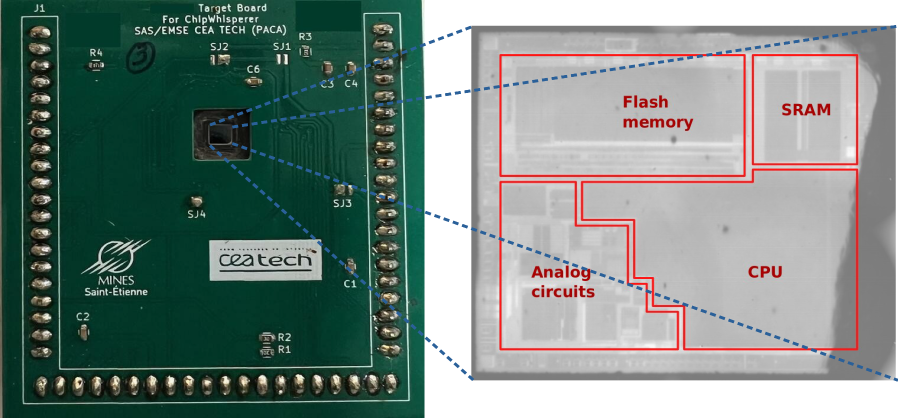
Figure 2 below:
Evolution of the number of faults in the Flash memory during X-Ray irradiations. Each blue dot corresponds to a Flash memory acquisition.
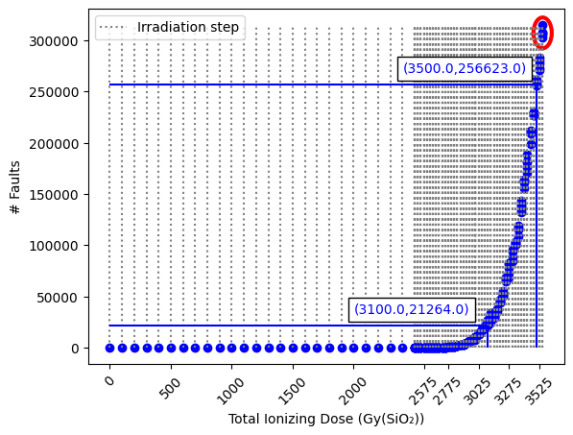
Figure 3 below:
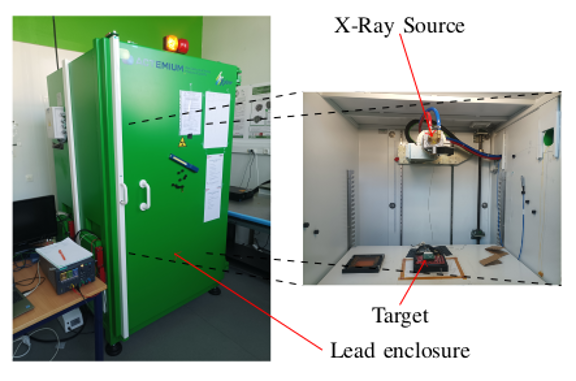
Picture of the irradiator.
Abstract
For several years, electronic components have taken an increasingly important place in our societies. Their security has become an dominant matter as they can contain sensitive data. To assess their security, new means of fault injection are set up. X-Ray effects on electronic devices have been studied for space applications but only a few recent papers deal with the security point of view. The state of the art shows that X-Ray can more easily have an effect on power off devices than other means of fault injection like laser injection or electromagnetic injection. This article gives experimental results on an X-Ray fault injection campaign on power off microcontrollers dedicated for IoT devices. Some of these X-Ray effects on the Flash embedded non-volatile memory of these microcontrollers highlighted in this study can be reversed performing thermal recuperation. This paper substantiates that the number of faults injected in a memory has an exponential dependency with the total ionizing dose according to a bitset fault model.
Read the full article here.