Research area
The research activities cover four important themes in the field of hardware architectures for applied cryptography and telecommunications:
- Generation of true random numbers and physically uncloneable functions in logic devices
- Hardware cryptographic architectures resistant to active and passive cryptographic attacks such as side-channel attacks
- Secure implementations of post-quantum schemes
- Systems on Chip security
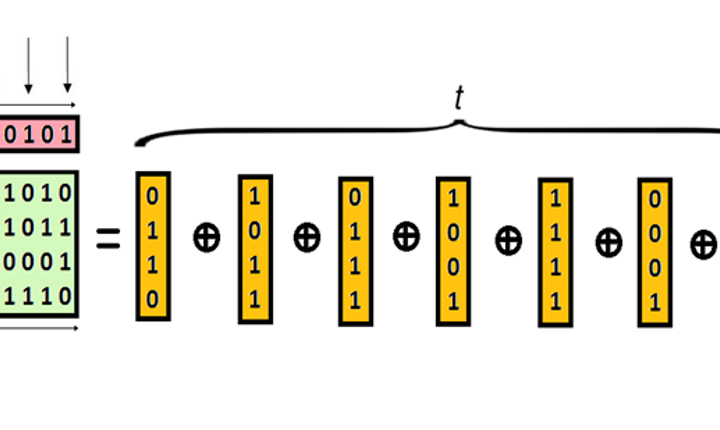
TRNGs and PUFsSecure true random number generation and physically uncloneable functions in logic devices aimed at cryptographic applications
True Random Number Generators (TRNGs), Physically Uncloneable Functions (PUFs) and related subjects represent the main stream of our scientific activities and this research area is further divided into four research axes:
- Identification of physical sources of randomness in logic devices and methods of randomness extraction
- Methods, tools and mathematical models aimed at characterization of the sources of randomness and randomness extraction
- Efficient embedded tests for on-line TRNG/PUF testing
- TRNG/PUF architectures aimed at implementation in logic devices
Side Channel AttacksHardware cryptographic architectures with increased resistance to active and passive cryptographic attacks
Research activities of our group in this general field of applied cryptography are oriented in five particular domains:
- Design of leakage resilient cryptographic schemes
- Side-channel cryptographic attacks and counter-measures, and in particular neural networks and deep learning applied to DPA
- Proposition of new cryptographic primitives and algorithms that are intrinsically resistant to cryptographic attacks
- Fault injection attacks and counter-measures
- Architectures of crypto-processors with secured key management
Code-based cryptoSecure implementations of post-quantum schemes
Code-based and lattice-based schemes offer a post-quantum security (there are no efficient attacks using a quantum computer).
- Implementation aspects of code-based and lattice-based schemes
- Proposition of new primitives for efficients implementations
- Side-channel analysis
- Theoretical aspects of exiting and new primitives.
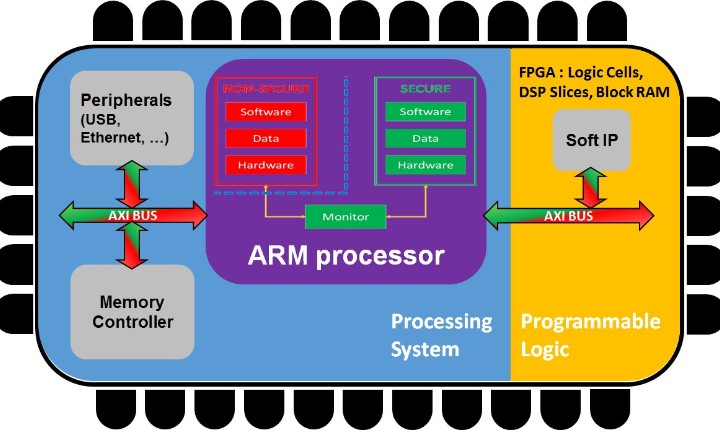
System on chip securityComplexe and heterogeneous SoC (FPGA+processor) security evaluation and protection
Research activities of our group in SoC security are oriented in four particular domains:
- Inside-SoC attacks using malicious hardware (fault injection, side channel analysis, covert channel)
- Complementary of hardware and software attacks to target heterogenous SoC
- Protection of heterogeneous SoC by design
- Architectures of crypto-processors with secured key management