Mateus Simões: Best Student Paper award at HOST 2023
Final year PhD student Mateus Simões has received a Best Student Paper award during the latest IEEE International Symposium on Hardware Oriented Security and Trust. The prize was awarded for his publication titled "Low-Latency Masking with Arbitrary Protection Order Based on Click-Elements".
After studying electrical engineering in Brazil, Mateus was granted a scholarship that allowed him to join the Ecole des Mines Saint-Etienne (EMSE) for a Master’s Degree in Microelectronics and Computer Science. Following a 6-month internship and a 6-month contract as a full-time engineer for the company STMicroelectronics, Mateus joined our lab to start a CIFRE thesis titled «Modeling and characterization of masking schemes resistant to side-channel attacks in the presence of glitches». The work, done under the supervision of Lilian Bossuet within our SESAM team, focusses on the design of secure and efficient microchips, offering cryptographic solutions to protect electronic devices against third parties.
Congratulations Mateus!
IEEE International Symposium on Hardware Oriented Security and Trust, HOST 2023
Low-Latency Masking with Arbitrary Protection Order Based on Click-Elements
Mateus Simões, Lilian Bossuet, Nicolas Bruneau, Vincent Grosso, Patrick Haddad and Thomas Sarno
In collaboration with STMicroelectronics, the team has studied architectural solutions to improve the latency of masking countermeasures. Indeed, side-channel attacks represent a threat to electronic systems designed to manipulate encrypted data. This class of security exploit allows an adversary to obtain sensitive information by observing the physical properties of a cryptographic device. In this manner, side-channel traces such as power consumption and electromagnetic emanation can be statistically analyzed to reveal secret data - e.g. the cipher key. To avoid side-channel attacks, various countermeasures exist. Masking, the most relevant among these solutions, splits secret data into several random shares, rendering more complex to predict the side-channel behavior of a cryptographic device. Despite its sound formal proof of security, implementing a secure masking scheme is not a straightforward task. To satisfy different design and security properties, an effective masking raises the latency of masked modules, i.e. the number of clock cycles needed to finish processing the data. In addition, the protected design requires higher area overhead due to the increase of the implementation complexity. However, with the increasing proliferation of IoT devices, secure low-latency and area-efficient cryptographic modules become therefore necessary to satisfy commercial demands. In this context, their work proposes a generic approach to design low-latency and area-efficient masking built upon the asynchronous hardware design methodologies. This hardware design methodology uses the so-called click element (see Figure 1), to produce local clock pulses, triggering its correspondent register at the appropriate time, and eliminating the need of a global clock signal within the data path. To meet the timing requirements of a given circuit, they apply the adaptive delay matching technique (see Figure 2), to synthesize their masked designs, achieving single-cycle evaluation of complex cryptographic functions with low implementation overhead.
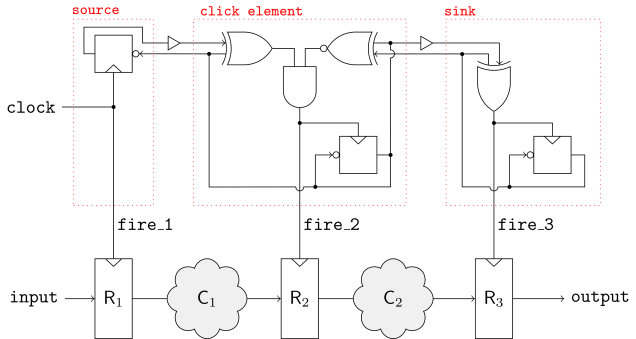
Figure 1 above: A simple pipeline with click elements.
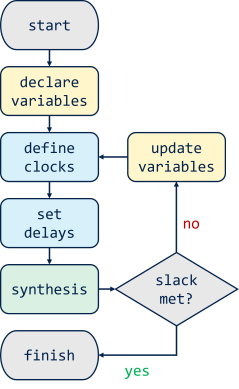
Figure 2 above: Synthesis flow with adaptive delay matching process.
Paper Abstract
Masking is the main countermeasure against sidechannel attacks due to its sound formal proof of security and the scalability of its protection parameters. However, effective masking increases the implementation complexity by requiring additional silicon area, random number generators and higher latency. Thus, reducing the masking implementation costs while conserving its robustness under side-channel attacks is a relevant branch of research in hardware security applications.
Relying on the two-phase bundled-data protocol, this work presents a low-latency masking implementation with arbitrary protection order. In particular, we base our approach on the click elements to control the handshake logic, allowing us to implement asynchronous circuits using conventional synthesis tools. In this manner, we are able to obtain an effective single-cycle and protected implementation of the AES S-box requiring smaller silicon area and potentially lower power consumption compared to the state-of-the-art. Additionally, we detail the asynchronous design methodology that can be applied in different scenarios to improve the latency of secure hardware designs. Finally, we assess leakages to evaluate the robustness of our approach against side-channel attacks.

